Beginners Guide to LUKS Disk Encryption in Linux
Let us talk about something on security hardening in Linux. the first topic that comes to mind is Disk encryption. The risk of a system’s physical compromise, particularly mobile systems such as laptops, puts sensitive data at risk of compromise. Encrypting the data mitigates the risk of its exposure if the system is lost.
LUKS (Linux Unified Key Setup-on-disk-format) is the standard for Linux hard disk encryption. By providing a standard on-disk-format, does not only facilitate compatibility among distributions but also provides secure management of multiple user passwords. In contrast to the existing solutions, LUKS stores all setup necessary setup information in the partition header, enabling the user to transport or migrate his data seamlessly.
What LUKS does:
- LUKS encrypts entire block devices and is therefore well-suited for protecting the contents of mobile devices such as removable storage media or laptop disk drives.
- The underlying contents of the encrypted block device are arbitrary. This makes it useful for encrypting swap devices. This can also be useful with certain databases that use specially formatted block devices for data storage.
- LUKS uses the existing device mapper kernel subsystem.
- LUKS provides passphrase strengthening which protects against dictionary attacks.
- LUKS devices contain multiple key slots, allowing users to add backup keys or passphrases.
What LUKS does not do:
- LUKS is not well-suited for applications requiring many (more than eight) users to have distinct access keys to the same device.
- LUKS is not well-suited for applications requiring file-level encryption.
Let us talk about to configure Disk encryption in Linux. If you want to configure the Disk encryption at the time of OS installation you could select the “Encrypt my data” checkbox in the Disk partitioning section on the install screen.
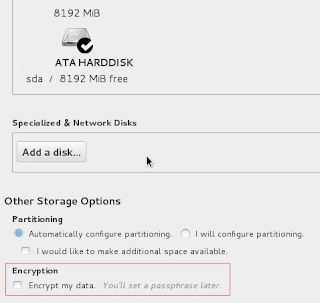
When performing automated installation using kickstart, one can create an encrypted partitions. Use –encrypted and –passphrase= options for each partition to be encrypted.For example, the following line would encrypt the /home partition.
# part /home --fstype=ext4 --size=10000 --onpart=vda2 --encrypted --passphrase=PASSPHRASE
Note the passphrase, PASSPHRASE is stored in the kickstart profile in plaintext. So the kickstart profile must be secured. Omitting the –passphrase= option will cause the installer to pause and ask for the passphrase during installation.
Here are the steps to configure encrypted volume after OS installation. First, check the cryptsetup utility is installed on the server or not. If not installed, then install it using yum or rpm commands.
cryptsetup-1.6.6-3.el7.x86_64 : A utility for setting up encrypted disks
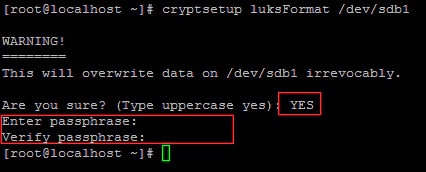
Create either a physical disk or a new logical volume. Here I am using /dev/sdb1 for creating an encrypted partition. Run the following command to create the encrypted partition. it will ask the Confirmation and then you need to put the passphrase to access the partition.
# cryptsetup luksFormat /dev/sdb1
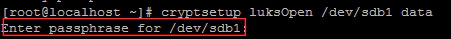
Now to access the Encrypted partition. you need to assign a logical name using the following command. it will ask you the passphrase.
# crypsetup luksOpen /dev/sdb1 name
Create a filesystem in the decrypted volume.
# mkfs -t ext4 /dev/mapper/name
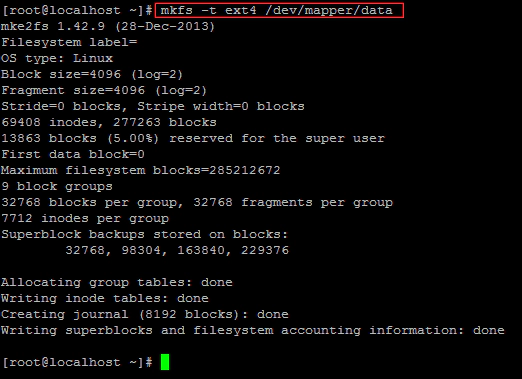
Create a mount point for the filesystem, mount it, then access the contents.
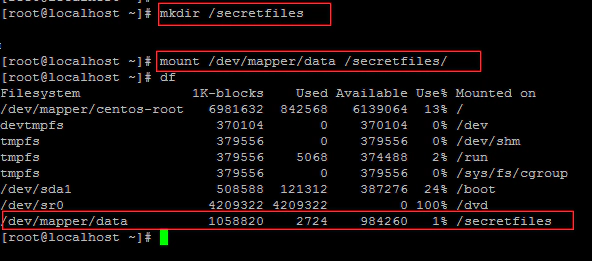
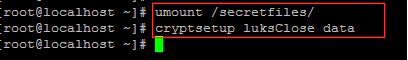
When finished, unmount the filesystem then lock the encrypted volume.
# umount /mountpoint
# cryptsetup luksClose name
All Good! That’s all you need to know to configure an encrypted volume. However, if a LUKS partition is created at the installation time, normal system operation prompts the users for the LUKS passphrase at the boot time. this is fine with a desktop or laptop, but not for the server that may need to be able to reboot unattended.
To boot a server with an encrypted volume unattended, a file must be created with a LUKS key that will unlock the encrypted volume. This file must be presented in an unencrypted filesystem on the disk. Of course this presents a security risk if the filesystem is on the same disk as the encrypted volume because theft of the disk would include the key need to unlock the encrypted volume, Typically the file with the key is stored in a removable media such as a USB key.
Here are the steps to configure a system to persistently mount an encrypted volume without human intervention. Locate or generate a key file. This is typically created with random data on the server and kept in a separate storage device. Make sure that this file is owned by root and permission is 600.
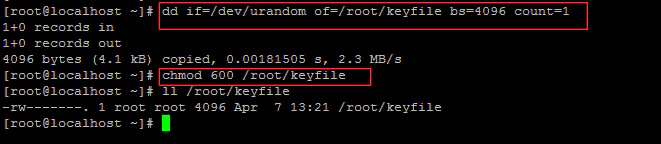
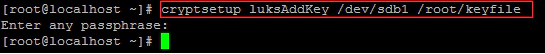
Add the key file to LUKS using the following command. and provide a passphrase used to unlock the encrypted volume when prompted.
# cryptsetup luksAddKey /dev/sdb1 /root/keyfile
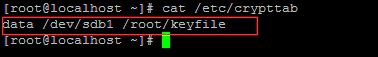
Create a /etc/crypttab entry for the volume. /etc/crypttab contains a list of devices to be unlocked during system boot.
Add an entry in /etc/fstab like the following.