Beginners Guide to Masquerading and Port Forwarding in CentOS/RHEL 7
Network Address Translatiob(NAT)
firewalld supports two types of Network Address Translation (NAT): masquerading and port forwarding. Both can be configured on a basic level with regular firewall-cmd rules, and more advanced forwarding configurations can be accomplished with rich rules. Both forms of NAT modify certain aspects of a packet, like the source or destination, before sending it on.
Masquerading
With masquerading, a system will forward packets that are not directly addressed to itself to the intended recipient, while changing the source address of the packets that go through to its own public IP address. When answers to those packets come in, the firewall will then modify the destination address to the address of the original host, and send the packet on. This is usually used on the edge of a network to provide Internet access to an internal network. Masquerading is a form of Network Address Translation (NAT).
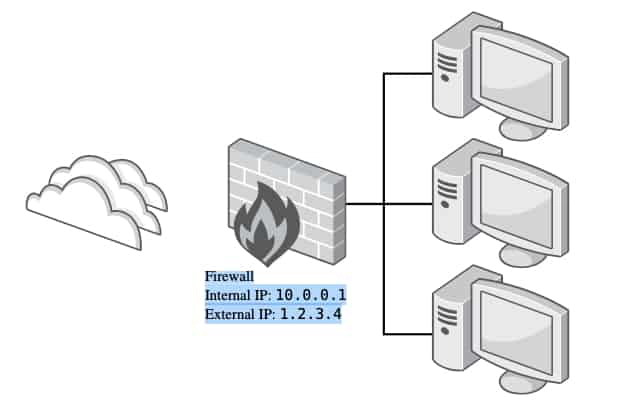
An example of how masquerading works based on the network layout described in the image above.
- One of the machines behind the firewall sends a packet to an address outside of the local network. The packet has a source address of 10.0.0.100 (the address of the machine), and a destination address of 2.17.39.214.
- Since the destination address is not on the local subnet, the packet will be routed to the default gateway configured on the source machine; in this case, 10.0.0.1, the IP address of the firewall.
- The firewall accepts the packet, changes the source address to 1.2.3.4 (the external IP for the firewall), stores a reference to this connection in its connection state table, then passes it to a router on the Internet based on its routing table.
- An answer to the packet comes back from the Internet. The router looks up the connection in its connection state table, then changes the destination address to 10.0.0.100 (the original sender), and passes the packet on.
- The original sender receives the answer to its request.
Configuring masquerading
To configure masquerading for a zone with regular firewall-cmd commands, use the following syntax:
# firewall-cmd --permanent --zone=[ZONE] --add-masquerade
This will masquerade any packets sent to the firewall from clients defined in the sources for that zone (both interfaces and subnets) that are not addressed to the firewall itself.
To gain more control over what clients will be masqueraded, a rich rule can be used as well.
# firewall-cmd --permanent --zone=[ZONE] --add-rich-rule='rule family=ipv4 source address=192.168.0.0/24 masquerade'
Port Forwarding
Another form of NAT is port forwarding. With port forwarding, traffic to a single port is forwarded either to a different port on the same machine or to a port on a different machine. This mechanism is typically used to “hide” a server behind another machine or to provide access to a service on an alternate port.
An example of a port forward based on the network layout described in the image. Assume that the machine with the IP address 10.0.0.100 behind the firewall is running a web server on port 8080/TCP, and that the firewall is configured to forward traffic coming in on port 80/TCP on its external interface to port 8080/TCP on that machine.
- A client from the Internet sends a packet to port 80/TCP on the external interface of the firewall.
- The firewall changes the destination address and port of this packet to 10.0.0.100 and 8080/TCP and forwards it on. The source address and port remain unchanged.
- The machine behind the firewall sends a response to this packet. Since this machine is being masqueraded (and the firewall is configured as the default gateway), this packet is sent to the original client, appearing to come from the external interface on the firewall.
Configuring port forwarding
To configure port forwarding with regular firewall-cmd commands, use the following syntax:
# firewall-cmd --permanent --zone=[ZONE] --add-forward-port=port=[PORTNUMBER]:proto=[:toport=[PORTNUMBER]][:toaddr=[IPADDR]]
Both the toport= and toaddr= parts are optional, but at least one of those two will need to be specified. As an example, the following command will forward incoming connections on port 513/TCP on the firewall to port 132/TCP on the machine with the IP address 192.168.0.254 for clients from the **public **zone:
# firewall-cmd --permanent --zone=public --add-forwardport=port=513:proto=tcp:toport=132:toaddr=192.168.0.254
To gain more control over port forwarding rules, the following syntax can be used with rich rules:
forward-port port=[PORTNUM] protocol=tcp|udp [to-port=[PORTNUM]] [toaddr=[ADDRESS]]
An example that uses rich rules to forward traffic from 192.168.0.0/26 in the work zone to port 80/TCP to port 8080/TCP on the firewall machine itself:
# firewall-cmd --permanent --zone=work --add-rich-rule='rule family=ipv4 source address=192.168.0.0/26 forward-port port=80 protocol=tcp toport=8080'