Beginners Guide to User and Group Administration on a Linux System
In this post and in future posts in the series, we will learn how to create, manage, and delete local users and groups and administer local password policies in a Linux system. In this first post, we will describe user and group concepts.
What is a User?
A user account is used to provide security boundaries between different people and programs that can run commands. Users have user names to identify them to human users and make them easier to work with. Internally, the system distinguishes user accounts by the unique identification number assigned to them, the user ID or UID. If a user account is used by humans, it will generally be assigned a secret password that the user will use to prove that they are the actual authorized user when logging in.
User accounts are fundamental to system security. Every process (running program) on the system runs as a particular user. Every file has a particular user as its owner. File ownership helps the system enforce access control for users of the files. The user associated with a running process determines the files and directories accessible to that process.
There are three main types of user account: the superuser, system users, and regular users.
- The superuser account is for administration of the system. The name of the superuser is root and the account has UID 0. The superuser has full access to the system.
- The system has system user accounts which are used by processes that provide supporting services. These processes, or daemons, usually do not need to run as the superuser. They are assiged non-privileged accounts that allow them to secure their files and other resources from each other and from regular users on the system. Users do not interactively log in using a system user account.
- Most users have regular user accounts which they use for their day-to-day work. Like system users, regular users have limited access to the system.
You can use the id command to show information about the currently logged-in user.
[user01@host ~]$ id
uid=1000(user01) gid=1000(user01) groups=1000(user01)
context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
To view basic information about another user, pass the username to the id command as an argument.
[user01@host]$ id user02
uid=1002(user02) gid=1001(user02) groups=1001(user02)
context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
To view the owner of a file use the ’ls -l’ command. To view the owner of a directory use the ’ls -ld’ command. In the following output, the third column shows the username.
[user01@host ~]$ ls -l file1
-rw-rw-r--. 1 user01 user01 0 Feb 5 11:10 file1
[user01@host]$ ls -ld dir1
drwxrwxr-x. 2 user01 user01 6 Feb 5 11:10 dir1
To view process information, use the ps command. The default is to show only processes in the current shell. Add the a option to view all processes with a terminal. To view the user associated with a process, include the u option. In the following output, the first column shows the username.
[user01@host]$ ps -au
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 777 0.0 0.0 225752 1496 tty1 Ss+ 11:03 0:00 /sbin/agetty -op -- \u --noclear tty1 linux
root 780 0.0 0.1 225392 2064 ttyS0 Ss+ 11:03 0:00 /sbin/agetty -op -- \u --keep-baud 115200,38400,9600
user01 1207 0.0 0.2 234044 5104 pts/0 Ss 11:09 0:00 -bash
user01 1319 0.0 0.2 266904 3876 pts/0 R+ 11:33 0:00 ps au
The output of the preceding command displays users by name, but internally the operating system uses the UIDs to track users. The mapping of usernames to UIDs is defined in databases of account information. By default, systems use the /etc/passwd file to store information about local users. Each line in the /etc/passwd file contains information about one user. It is divided up into seven colon-separated fields. Here is an example of a line from /etc/passwd:

- Username for this user (user01).
- The user’s password used to be stored here in encrypted format. That has been moved to the /etc/shadow file, which will be covered later. This field should always be x. The UID number for this user account (1000).
- The GID number for this user account’s primary group (1000).Groups will be discussed later in this section.
- The real name for this user (User One).
- The home directory for this user (/home/user01). This is the initial working directory when the shell starts and contains the user’s data and configuration settings.
- The default shell program for this user, which runs on login (/bin/bash). For a regular user, this is normally the program that provides the user’s command-line prompt. A system user might use /sbin/nologin if interactive logins are not allowed for that user.
Whats is a Group
A group is a collection of users that need to share access to files and other system resources. Groups can be used to grant access to files to a set of users instead of just a single user. Like users, groups have group names to make them easier to work with. Internally, the system distinguishes groups by the unique identification number assigned to them, the group ID or GID.
The mapping of group names to GIDs is defined in databases of group account information. By default, systems use the /etc/group file to store information about local groups. Each line in the /etc/group file contains information about one group. Each group entry is divided into four colon-separated fields. Here is an example of a line from /etc/group:
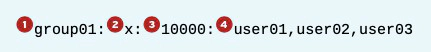
- Group name for this group (group01).
- Obsolete group password field. This field should always be x.
- The GID number for this group (10000).
- A list of users who are members of this group as a supplementary group (user01, user02, user03). Primary (or default) and supplementary groups are discussed later in this section.
Primary Groups and Supplementary Groups
Every user has exactly one primary group. For local users, this is the group listed by GID number in the /etc/passwd file. By default, this is the group that will own new files created by the user. Normally, when you create a new regular user, a new group with the same name as that user is created. That group is used as the primary group for the new user, and that user is the only member of this User Private Group. It turns out that this helps make management of file permissions simpler, which will be discussed later in this course.
Users may also have supplementary groups. Membership in supplementary groups is determined by the /etc/group file. Users are granted access to files based on whether any of their groups have access. It doesn’t matter if the group or groups that have access are primary or supplementary for the user. For example, if the user user01 has a primary group user01 and supplementary groups wheel and webadmin, then that user can read files readable by any of those three groups. The id command can also be used to find out about group membership for a user.
[user03@host ~]$ id
uid=1003(user03) gid=1003(user03) groups=1003(user03),10(wheel),10000(group01)
context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
In the preceding example, user03 has the group user03 as their primary group (gid). The groups item lists all groups for this user, and other than the primary group user03, the user has groups wheel and group01 as supplementary groups.